
LockBit 3.0 Attacked Bank Syariah Indonesia Massively
By Agastya W.
Published on April 20, 2023
Bank Syariah Indonesia reported data theft by the dangerous community called Lockbit 3.0 on May 8.
Customers of BSI complained about the transaction activity being cut off for four days on the company’s online banking system.
This ransomware outbreak has stolen 1.5 million customer and employee databases, totaling 1.5 terabytes of data.
Teguh, the founder of Ethical Hacker Indonesia, claims that LockBit 3.0’s ransomware will cause serious damage in the future.
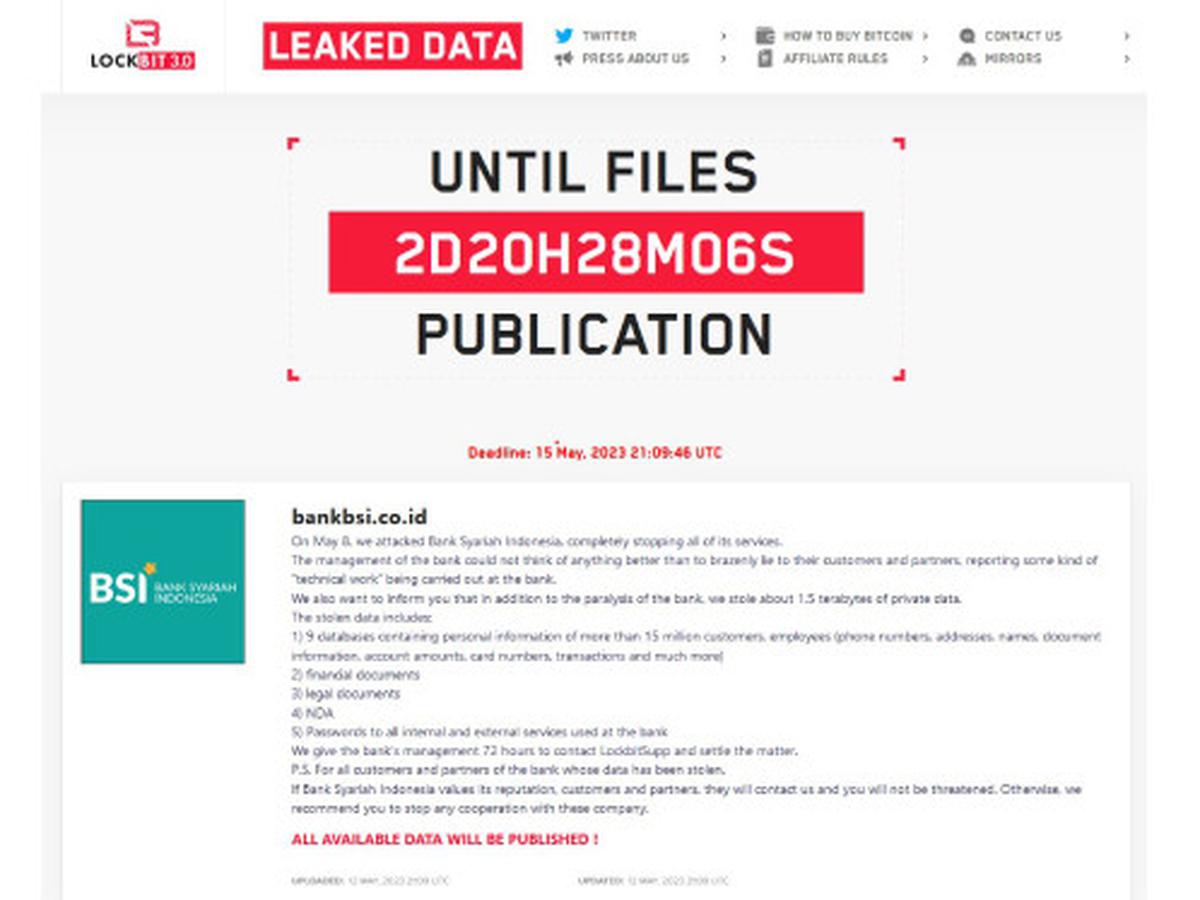
Image source: liputan6.com
Who is LockBit 3.0?
LockBit 3.0 is a cybercriminal group that works for companies or individuals to attack a particular organization by spreading a dangerous virus – ransomware.
The ransomware virus employs encryption to steal data. If the victim requests their data back, only LockBit 3.0 is possessed the key to decrypt and make it available.
Instead, Lockbit will demand payment in the form of a ransom.
LockBit 3.0 Crime Record
BSI is not the first case of ransomware. With 1.500 victims, the organization has shattered the record for the most active ransomware group in 2023. More than 300 people have now become victims.
Atento, a CRM company, became a LockBit victim in 2021. In the financial performance report, the company lost $ 42,1 million. And it has paid a total of $7,3 million in mitigation expenditures.
Furthermore, some famous companies that became the victim are SpaceX, English Royal Mail, Malaysian education institute, Sydney healthcare institute, and many more.

Indonesian Expertise Point of View
BSI (Bank Syariah Indonesia) is the biggest Syariah bank in Indonesia. Currently, BSI has 1.785 ATMs with more than 15 million customers around Indonesia.
It has been a question, what happens with BSI’s infrastructure?
According to Teguh in Kompas Bisnis‘s interview, there was a problem with BSI’s infrastructure. So that ransomware viruses can occur.
He also said, in general, banking downtime is not more than a day to be fixed. When it comes to four days, Teguh said it must be ransomware on their main server and backup server.
How to Face Ransomware
Although the issue has been resolved, the data leakage cannot be restored. It reaches citizens as well as hackers.
Cybercriminals can exploit the data to commit identity theft, illegal money lending, fraud, and other crimes.
The only way to face ransomware is to improve IT infrastructure. Such as having a mitigation plan, a good and secure infrastructure performance, also a damage control expert.
Now, it is time to create a better IT environment from both sides: Company and regulator.


